Web & Android Implementation
The SEADMv2 model was implemented as both a Web application (Figure 1) and an Android application (Figure 2) by Michael Pepper and Marcel Teixeira respectively. The aim with these implementations was to use them to perform experiments that determine whether they are effective at reducing the number of instances where subjects fell victim to social engineering attacks. The goals of these experiments can be found in the section to follow.
To perform the experiments, a Google Form was used which presented subjects with 10 potential social engineering attack scenarios. Users had to select a multiple choice answer for each scenario that best depicted how they would react to those scenarios. Upon completion of this stage of the experiment, users were presented with the same 10 scenarios, however, now they had to make use of the tool to guide their answers to the scenarios. Upon completion of this stage, the resulting document contained an indication of how subjects responded to potential social engineering attack scenarios with and without the use of the model. This information was then statistically analysed to determine whether the model had an overall positive effect on reducing the number of instances that subjects fell victim to social engineering attacks, and whether it adversely affected the number of harmless scenarios that were satisfied. The results of these experiments can be found below.


Project Goals
We aim to determine whether:
- A Web-based implementation of the SEADMv2 can reduce the number of intsances that a subject falls victim to social engineering attacks, while increasing the number of harmless requests that are sattisfied.
- An Android application of the SEADMv2 can reduce the number of intsances that a subject falls victim to social engineering attacks, while increasing the number of harmless requests that are sattisfied.
Results
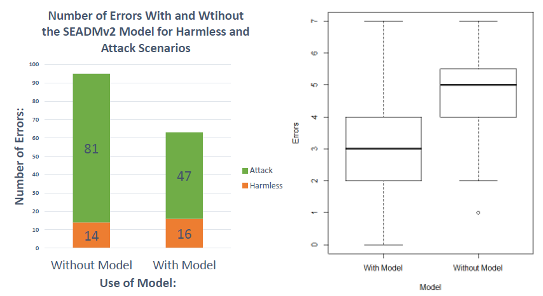
The Web-based implementation of the SEADMv2 yielded the following results:
- A significant reduction in the overall number of errors made on potential social engineering attack scenarios.
- A significant reduction in the overall number of instances that a subject fell victim to social engineering attacks.
- No significant change in the number of harmless requests that were sattisfied by subjects.
- A significant reduction in the number of instances that subjects fell victim to social engineering attacks that are indirectly and bidirectionally communicated, however, no effect was established on unidirectionally communicated attacks.
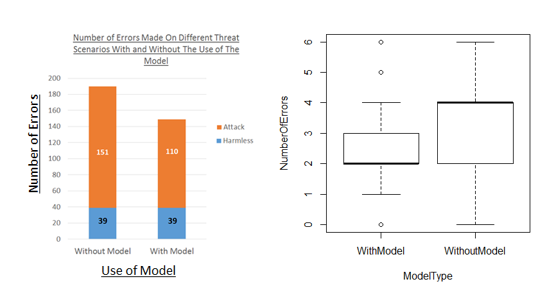
The Android implementation of the SEADMv2 yielded the following results:
- A significant reduction in the overall number of errors made on potential social engineering attack scenarios.
- A significant reduction in the overall number of instances that a subject fell victim to social engineering attacks, however, no significant change in the number of harmless requests that were satisfied by the subjects.
- A significant reduction in the number of instances that subjects fell victim to social engineering attacks that are indirectly and bidirectionally communicated, however, no effect was established on unidirectionally communicated attacks.