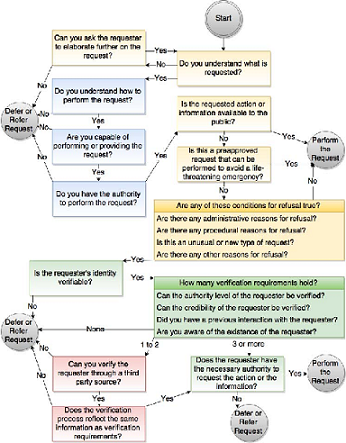
Social Engineering Prevention Training Tool
Information security is constantly evolving, with technical safeguards being upgraded on a daily basis to mitigate the possibility of malicious attacks. This has caused some attackers (Social Engineers) to shift their focus to the new most vulnerable point in the information security system – the user. The average person is often not aware of the types of attacks that they may be subjected to, as well as what action to take in these attacks. There are also currently no tools available that can be used to detect social engineering attacks, leaving the general public in a vulnerable position. The SEPTT project aims at addressing this by implementing the Social Engineering Attack Detection Model version 2 (SEADMv2 - shown below) proposed by Mouton et al. [1] in order to provide people with a tool that they can use in any situation to determine if they are being subjected to acts of social engineering. This tool provides guidance to users as to how they should respond to a given scenario, according to whether it is deemed to be malicious or harmless. This was achieved by implementing the SEADMv2 as a Web Application and an Android Application. Experiments were then performed with each implementation to determine if they were effective at reducing the number of instances that subjects fell victim to social engineering attacks.